You're about to recycle your laptop or your phone, so you delete all your photos and personal files. Maybe you even reset the device to factory settings.
Author
- Ritesh Chugh
Associate Professor, Information and Communications Technology, CQUniversity Australia
You probably think your sensitive data is now safe. But there is more to be done: hackers may still be able to retrieve passwords, documents or bank details, even after a reset.
In fact, 90% of second-hand laptops, hard drives and memory cards still contain recoverable data. This indicates that many consumers fail to wipe their devices properly before resale or disposal.
But there are some simple steps you can take to keep your personal information safe while recycling responsibly.
The data security risks
Discarded or resold electronics often retain sensitive personal and corporate information. Simply deleting files or performing a factory reset may not be sufficient. Data can often be easily recovered using specialised tools. This oversight has led to alarming incidents of data leaks and breaches.
For example, 42% of used storage devices sold on eBay still contained sensitive data, despite sellers following methods to erase data. This included passport images, school records, and corporate documents.
Another 2022 study found that improperly erased internet-connected devices stored private data, making them vulnerable to exploitation. European e-waste exported to Ghana also contained classified corporate and government files, exposing security risks beyond personal identity theft.
A major wireless provider in the United States failed to securely decommission storage devices . This lead to a data breach affecting 14 million customers.
Similarly, in 2021 improperly discarded medical hard drives exposed over 100,000 confidential patient records.
Why standard factory resets are not enough
Many people believe performing a factory reset fully erases their data. But this is not always the case.
An analysis of secondhand mobile devices found that 35% still contained recoverable data after being reset and resold. This highlights the risks of relying solely on factory resets.
On older devices or those without encryption, residual data can still be recovered using forensic tools.
iPhones use hardware encryption, making resets more effective, while Android devices vary by manufacturer.
Best practices for secure disposal
To protect your personal and organisational information, consider these measures before disposing of old devices:
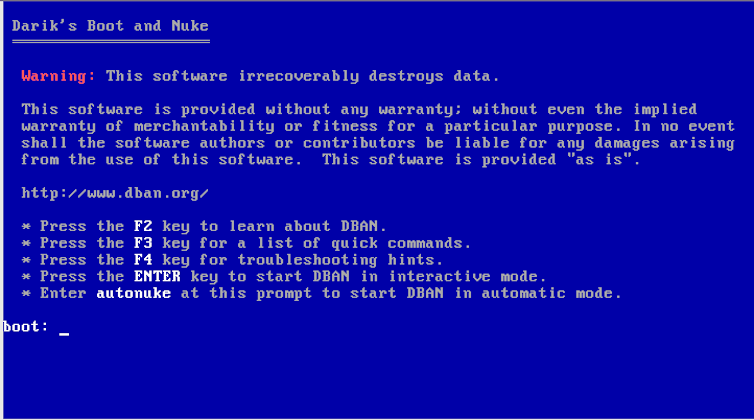
Data wiping
Personal users should use data-wiping software to securely erase their hard drive before selling or recycling a device.
However, for solid-state drives, traditional wiping methods may not be effective. This is because solid-state drives store data using flash memory and algorithms, which prolong a device's lifespan by distributing data across memory cells and can prevent direct overwriting.
Instead, enabling full-disk encryption with software such as BitLocker on Windows or FileVault on Mac before resetting the device can help to ensure data is unreadable.
On Android phones, apps such as Shreddit provide secure data-wiping options. iPhones already encrypt data by default, making a full reset the most effective way to erase information.
Businesses that handle customer data, financial records or intellectual property must comply with data protection regulations. They could use certified data-wiping tools that meet the United States National Institute of Standards and Technology's guidelines for media sanitisation or the US Institute of Electrical and Electronics Engineers' standard for sanitising storage . These guidelines are globally recognised.
Many companies also choose third-party data destruction services to verify compliance and enhance security.
Physical destruction
If the data is highly sensitive, physically destroying the storage medium (such as a hard drive) is the most secure option. Common methods include degaussing (using a strong magnetic field), shredding, disintegration, melting, and drilling.
However, some of these techniques can be hazardous if not handled by professionals. They also make a hard drive or device unsuitable for resale and instead require it to be taken to a waste recovery centre so the rare earth metal components can be recovered.
Certified recycling services
Use reputable e-waste recyclers who adhere to strict data destruction protocols to ensure your information does not fall into the wrong hands. Look for certifications such as R2, e-Stewards, or AS/NZS 5377, which ensure compliance with industry security standards. An online database run by sustainable electronics organisation SERI of R2-certified facilities around the world can help with this.
Safe selling and donating practices
Before selling or donating devices, conduct a thorough data wipe. Be cautious of devices linked to cloud accounts, and remove all personal information to prevent unauthorised access. Resetting alone may not be enough.
Legal and regulatory considerations for businesses
Different regions have strict data-protection laws that impose legal and financial penalties for improper disposal of sensitive data.
It's important for businesses to consider the legal standards for handling and disposing personal information in whatever region they're operating in, whether that be Europe , the United States , Australia or elsewhere.
Before recycling or selling an old device, take the necessary steps to ensure your data is completely erased. Identity theft, financial fraud and data breaches are real risks. But they can be prevented with the right precautions.
A few extra steps now can protect your information and ensure responsible recycling.
![]()
Ritesh Chugh does not work for, consult, own shares in or receive funding from any company or organisation that would benefit from this article, and has disclosed no relevant affiliations beyond their academic appointment.






